Product
Compliance Simplified
Simplify compliance with Trustle’s advanced reporting.
Trustle makes compliance and audits effortless by unlocking visibility and access request history for accurate audit reporting.
In an ideal world, these integrated systems and applications would individually provide the necessary information to satisfy audit requirements.
In reality, most organizations end up relying on spreadsheets and other costly tools that don't check all the required boxes.
These regulations emphasize access policy governance and the enforcement of zero standing privilege and least privilege access, both of which are crucial for continuous compliance.
Manually collecting and analyzing this data puts a strain on compliance teams who struggle to keep up.
This can leave organizations vulnerable to security threats that could otherwise be addressed.
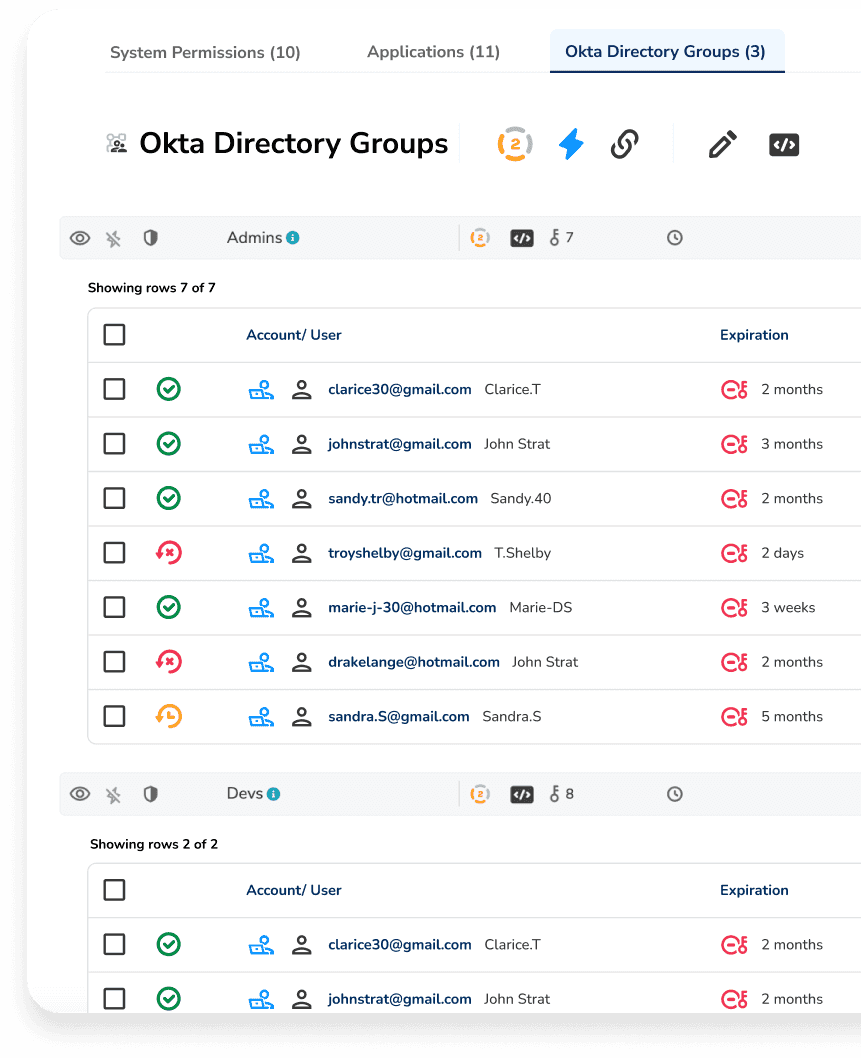
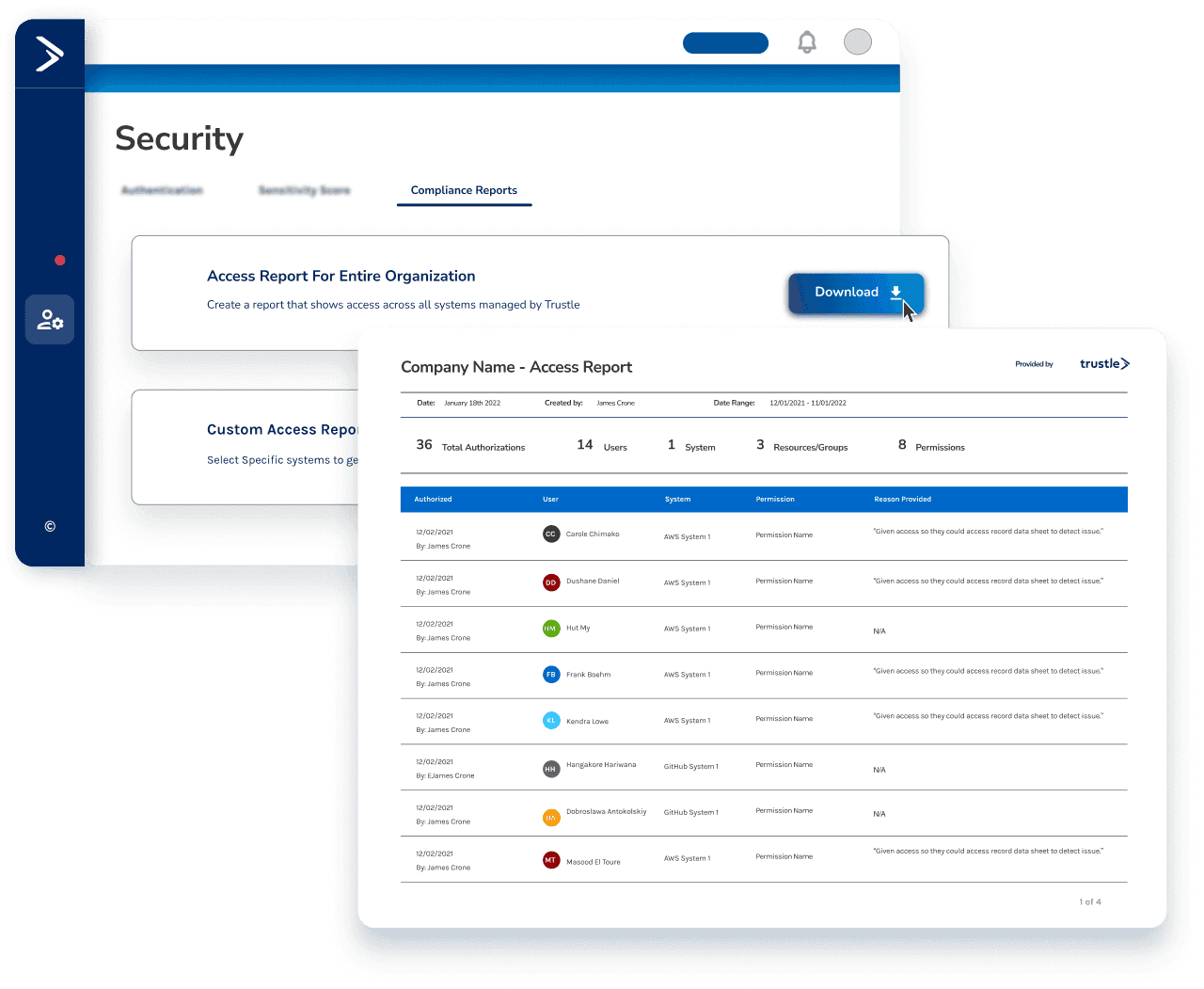
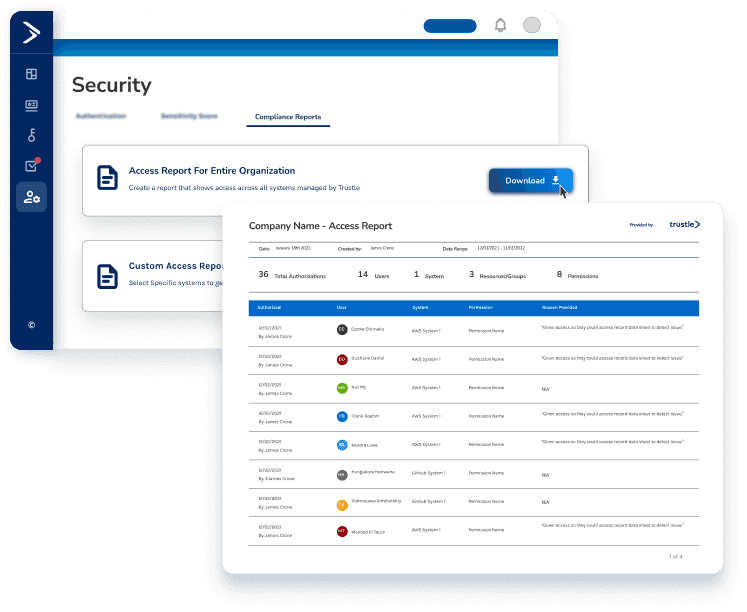
Trustle generates comprehensive access review reports that provide all the necessary information for your auditors, making it easier to stay compliant with regulatory requirements.
Our automated risk assessment provides a holistic view of each SaaS and Cloud environment, identifying risks and misconfigurations, and our machine learning technology detects anomalous access requests and well-known risks.
With Trustle, you get a deep, multi-dimensional, searchable view of all employee, contractor, customer, and system identities, resources, and entitlements for each of your connected environments. This empowers you to make informed decisions based on your current security posture.
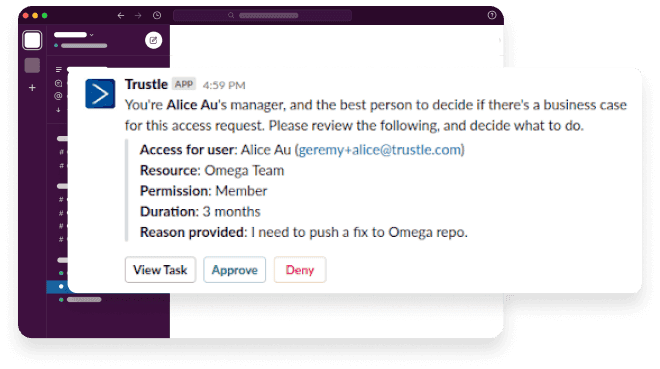
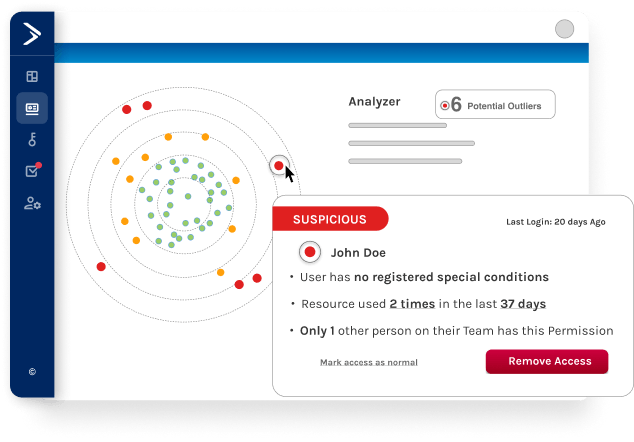
Whether its anomalous behavior, errant usage patterns, suspicious activity, or potential threats, Trustle provides proactive alerts, allowing you to take immediate action and mitigate risks before they become a significant problem.
When it comes to audits, Trustle's got you covered. Trustle provides detailed reports that help you stay compliant with industry regulations, saving you time and resources that would otherwise be spent on manual compliance reviews.

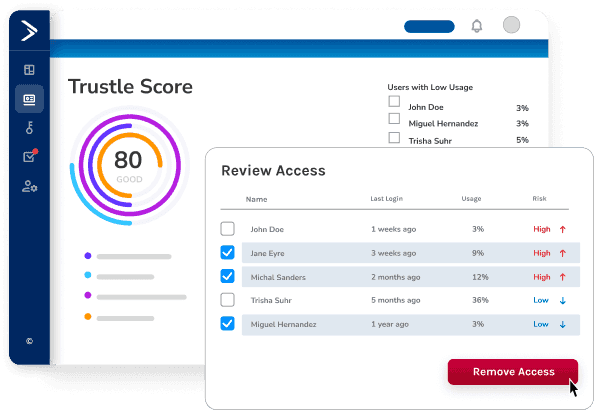
Trustle also helps you identify unused, underutilized, and abandoned accounts, reducing the attack surface of your systems and enhancing your overall security posture.
Trustle enforces zero standing privilege until least privileged, JIT access is required, ensuring your users only have the minimal access they need, when they need it. All steps of the JIT workflow, including request, approval, denial, provisioning, and revocation are logged, and made available for export in PDF and CSV formats.