Use Cases
Why you need us now
Trustle customers improve security, get more work done, and save money while doing it.
208 days
The average time it takes companies to identify an identity data breach.
1/3 of all breaches
are caused by over entitled access.
$3.6 million
The average amount companies saved in security costs that used least privilege access.
Problem Statement
We are a startup with a small team, we can’t introduce a complex process to enable our devs to do their jobs.
How can I implement a JIT access solution without bottlenecking the access requestors?
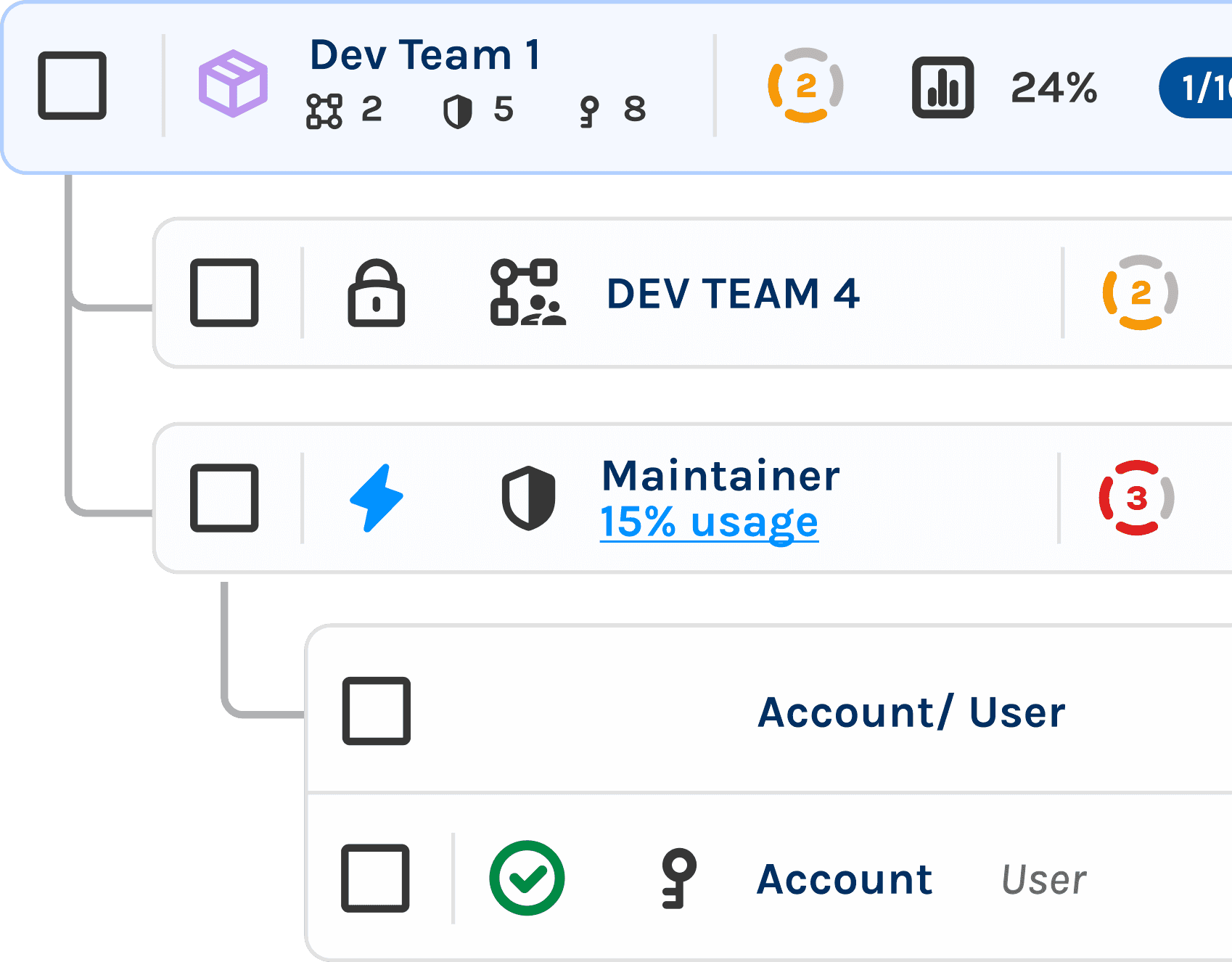
Trustle Packs
Trustle allows a designated Owner to grant and revoke a set of entitlements called a Trustle Pack. We allow Managers to do this now, which is a form a delegation in our policies.
With Trustle, you can take a distributed, proactive context-based approach to multi-cloud risk management.
Your teams have limited time and resources, and can't have JIT access workflows slow them down.
Trustle helps accelerate the least privilege access request workflow by allowing you to delegate the authority to trusted individuals within your organization who have the necessary context to approve or deny tasks. This gives you better control over your cloud environment while simultaneously empowering your employees to be more productive.
Want to request access to resources for a co-worker who will be helping you troubleshoot an issue?
Problem Statement
Our Operations team needs immediate access to production environments when a service disruption occurs.
How can I automate this access approval without the risk of standing access for the entire team?
With Trustle's multi-cloud context-based access management workflow solution, enterprises can streamline time-based, on-call duty access.
On-call events are unexpected and staff must be prepared to troubleshoot and remediate nearly any issue. The one issue they should never have to think about fixing is making sure they have the proper access required to do their job.
By approving least privilege access to production systems at rotation time, while enforcing zero standing access to those systems until an on-call event is triggered, Trustle automates on-call access, ensuring that engineers have proper access to resources during incidents. This reduces incident downtime and increases the security of your cloud environment.
In addition, to comply with security and privacy regulations like CIS, SOC2, and HIPAA, Trustle also provides a paper trail of on-call-related incident access in the form of workflow logs and compliance reports.
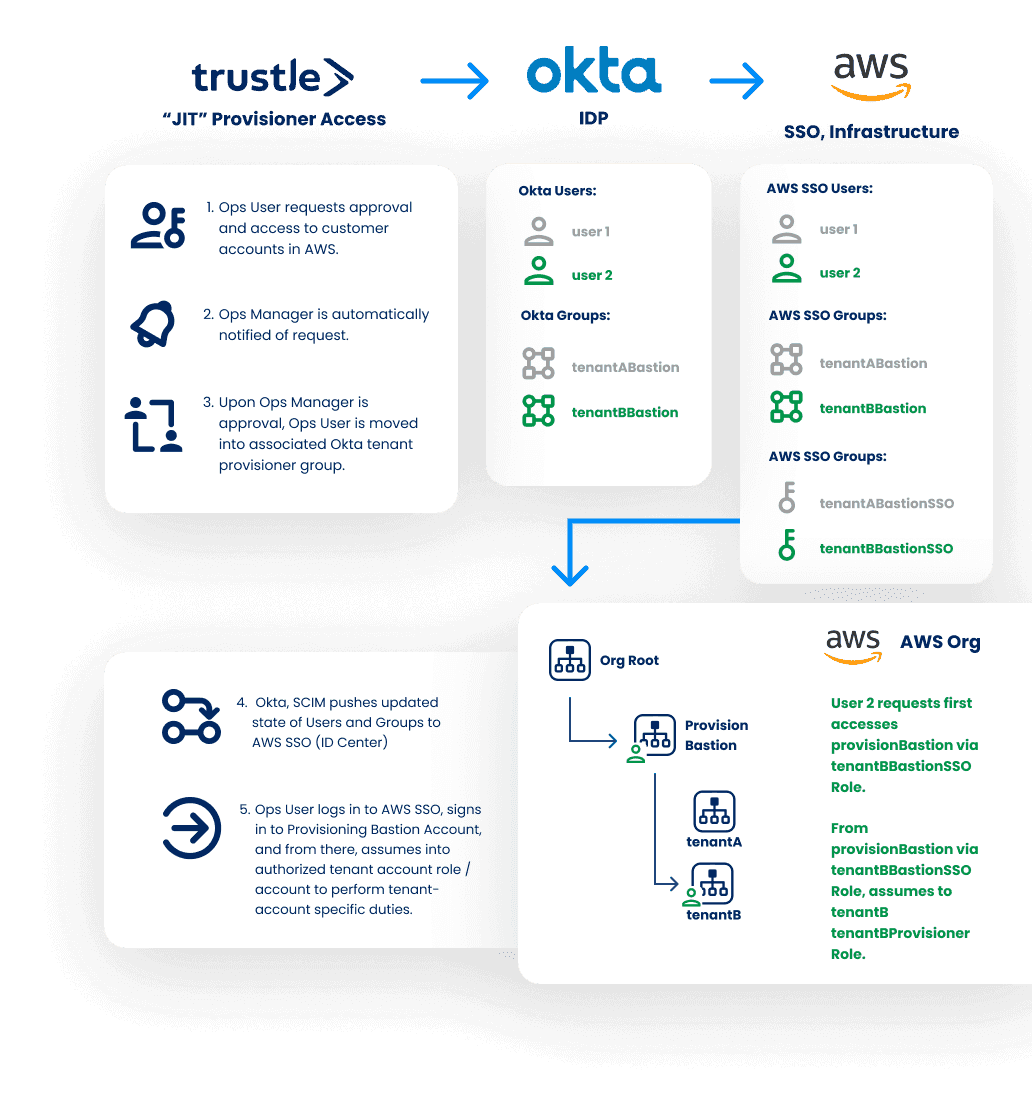
Problem Statement
I use AWS SSO with an external IdP like Okta… how can I grant a specific user access to a specific IdP group fronted by AWS SSO?
Trustle works seamlessly in environments which utilize Single Sign On (SSO).
Whether your IdP and SSO system are one in the same (for example, if you use Okta for App Login and IdP), or if you are using SCIM to synchronize your user and group data to an external SSO, like in the case of an Okta / AWS IAM Identify Center (AWS SSO) integration
Trustle’s got you covered!