Product
Just-In-Time Access
(JIT)
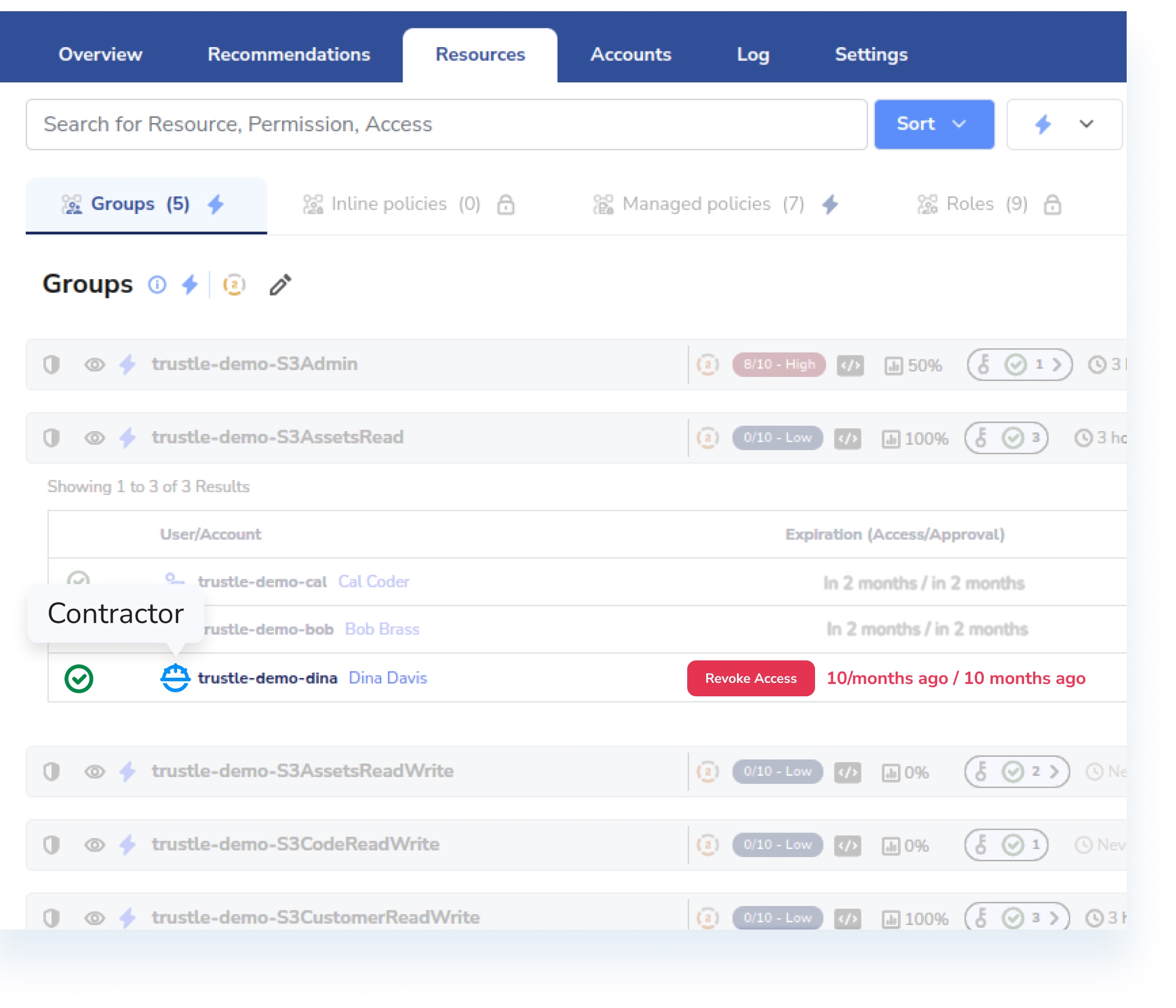
Keeping track of who has access across all your cloud-based services far exceeds human capacity.
approving access without context. Increasing the risk of approving unusual or suspicious activity.
but it becomes even more burdensome when you include contractors, Customer-based accounts, and System-based accounts.
Identify who has access to what in your environment, with context into access policies and approvals.
Detect identity risks - shadow users, overprivileged accounts, unnecessary standing access - and mitigate potential issues.
Enable seamless risk-based JIT access workflows, with built in expiration and revocation.
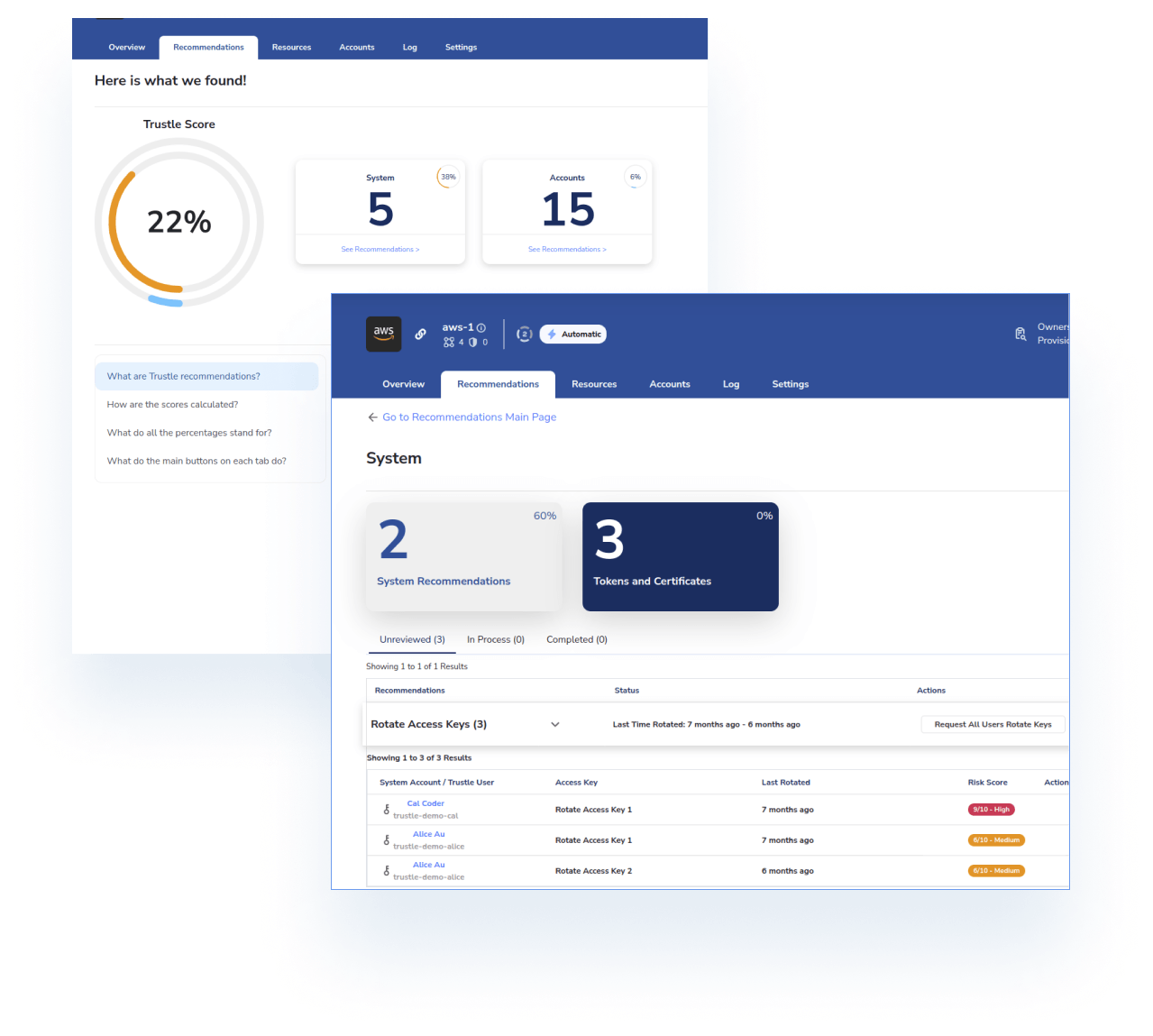
With Trustle, you can take a distributed, proactive approach to access management and stay ahead of potential threats to your cloud environment with just-in-time access.
By identifying and addressing risks, you can reduce the likelihood of accidental exposures, ensuring that your organization remains secure.
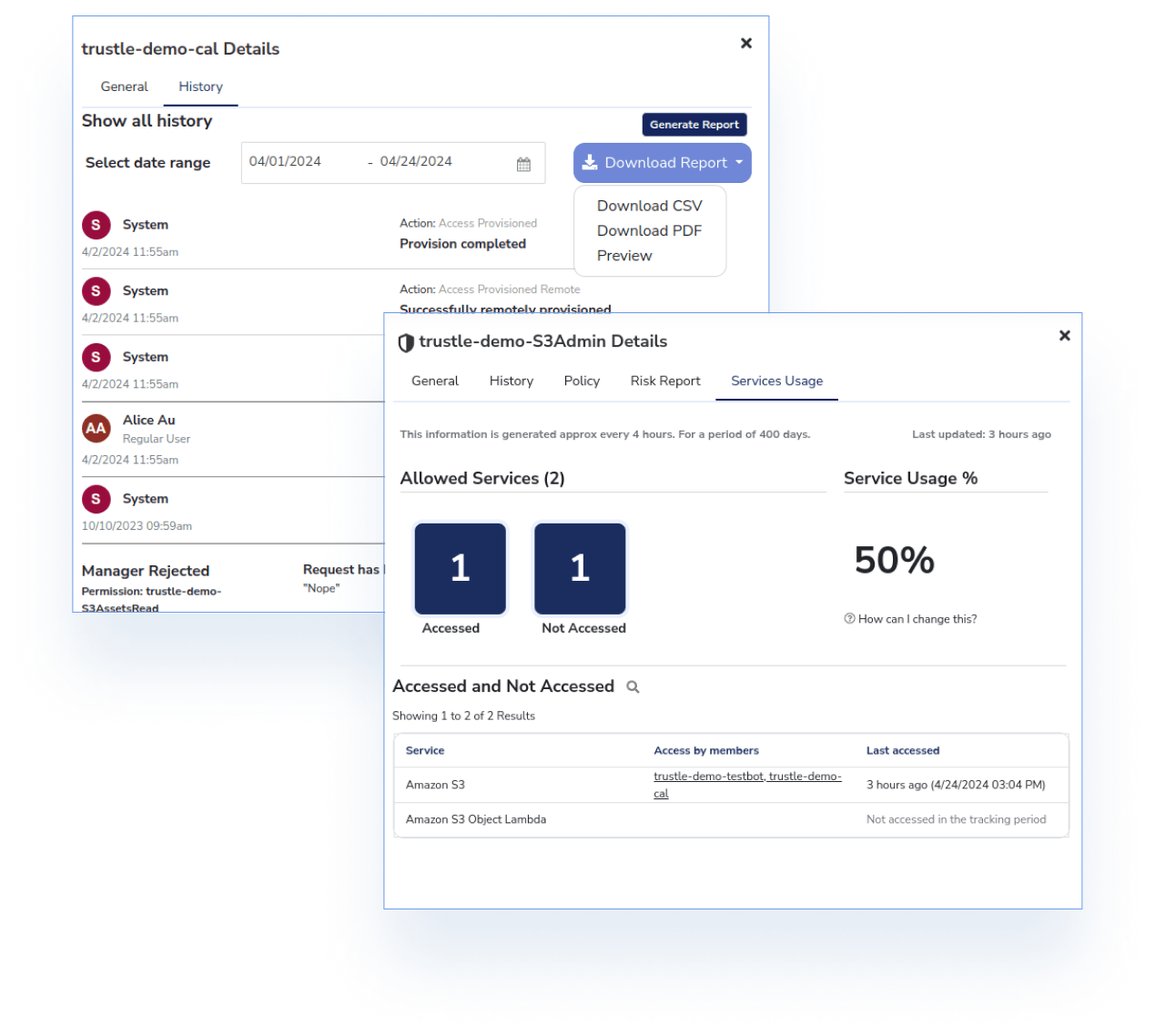
Trustle helps you approach risk proactively, providing compliance and access history reports to keep key stakeholders informed.
For management and systems owners, these reports facilitate policy-related discussions and changes, making it easier to stay on top of security. For auditors, these reports provide an automated method of generating evidence of regulatory compliance.
Our automated assessment provides a holistic view of each SaaS and Cloud environment, identifying risks and misconfigurations, and our machine learning technology detects anomalous and potentially threatening access requests, in addition to well-known risks.
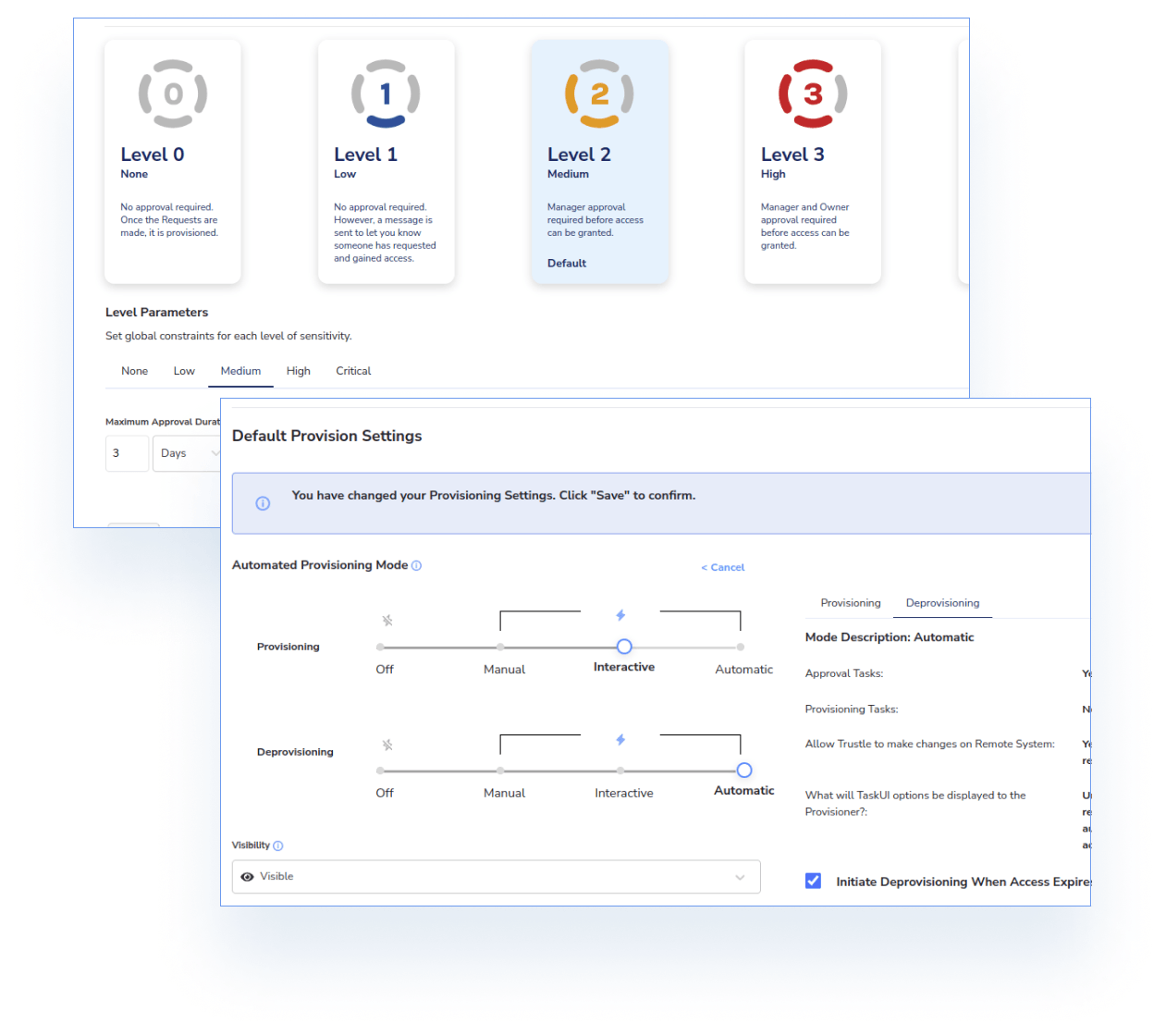
Trustle also offers flexible and convenient methods for risk remediation. Once you understand your security posture and attack surface, Trustle provides multiple options for automatic access-related mitigation.
Trustle is quick and easy to set up, taking only minutes instead of weeks.